Phoenix Arm Zero
June 19, 2023
Now that I have rounded off the stack challenges, now I will move on to the Format Strings challenges. Format Strings is a vulnerability where the input of the user is not santizied for special characters correctly, allowing the input to be a “format” string telling the program what kind of string should be returned. This can create situations where the user can read or modify memory.
In the first challenge, the objective is simply to change a variable which the user does not have direct control over. Taking a look at the source code, we can see there is an ‘sprintf’ call which attempts to print the contents of buffer into locals.dest.
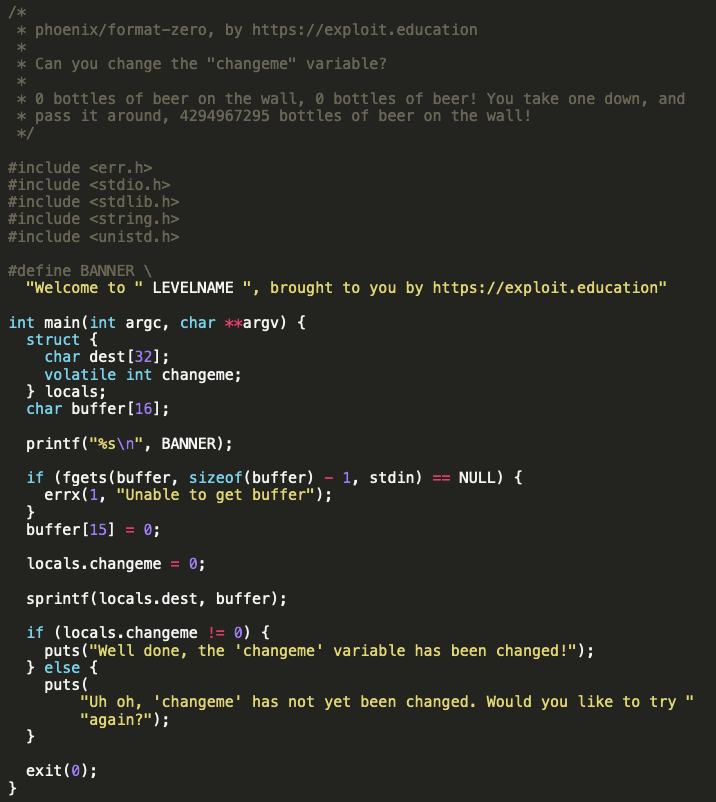
Within the locals struct, we can see the char buffer dest and integer changeme. We want to overwrite changeme, and we have 32 characters to fill the dest buffer with before we can do this. However, our input buffer is only 16 characters long. How can we overcome this?
As I mentioned before, a format strings vulnerability allows for us to tell the program what format of input we are trying to supply. Due to this issue, we can provide input which, when interpreted by the machine, will fill the dest buffer (during the sprintf) with information of the size we are providing.
In this example, I decided to use the “%x” format. I can only provide up to 16 of these, however each %x will fill 8 bytes of the dest buffer, thus providing the overflow to change the changeme variable.
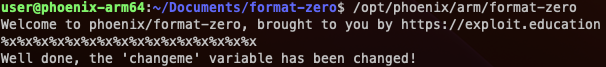
Success.
@andr01d@defcon.social